Good Day,
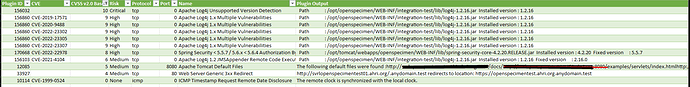
My organization makes use of Nessus vulnerability scanner and recent scan picked up that Openspecimen server reportedly have some vulnerabilities namely Log4J and Tomcat - please see attached screenshot.
Could you please provide guidance on what can be done to mitigate these reported vulnerabilities. We have upcoming CyberEssentials Plus audit and External/Internal Penetration Tests and we afraid this will get flagged.